Table of contents
AWS (Amazon Web Services) is a comprehensive, evolving cloud computing platform provided by Amazon that includes a mixture of infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS) and packaged-software-as-a-service (SaaS) offerings. AWS services can offer an organization tools such as compute power, database storage and content delivery services.
More than 200 services comprise the AWS portfolio, including those for compute, databases, infrastructure management, application development and security.
Some of the key services offered by AWS include:
1. Amazon EC2 (Elastic Compute Cloud)
EC2 is a cloud platform provided by Amazon that offers secure, and resizable compute capacity. Its purpose is to enable easy access and usability to developers for web-scale cloud computing, while allowing for total control of your compute resources.
Deploy applications rapidly without the need for investing in hardware upfront; all the while able to launch virtual servers as-needed and at scale.
2. Amazon RDS (Relational Database Services)
Amazon Relational Database Service (Amazon RDS) makes database configuration, management, and scaling easy in the cloud. Automate tedious tasks such as hardware provisioning, database arrangement, patching, and backups – cost-effectively and proportionate to your needs.
RDS is available on various database instances which are optimized for performance and memory, providing six familiar database engines including Amazon Aurora, PostgreSQL, MySQL, MariaDB, Oracle. database, and SQL server. By leveraging the AWS Database Migration Service, you can easily migrate or reproduce your existing databases to Amazon RDS.
3. Amazon S3 (Simple Storage Service)
Amazon S3, at its core, facilitates object storage, providing leading scalability, data availability, security, and performance. Businesses of vast sizes can leverage S3 for storage and protect large sums of data for various use cases, such as websites, applications, backup, and more.
Amazon S3’s intuitive management features enable the frictionless organization of data and configurable access controls.
4. Amazon Lambda
Lambda permits you to run code without owning or managing servers. Users only pay for the compute time consumed.
Operate code for nearly any application or backend utility without administration. Users just upload the code, and Lambda does the rest, which provides precise software scaling and extensive availability.
5. Amazon Cognito
AWS Cognito administers a control access dashboard for on-boarding users through sign-up, and sign-in features to their web and mobile apps. AWS Cognito scales to millions of users and offers sign-in support with social identity providers including Facebook, Google, and Amazon, along with enterprise identity providers via SAML 2.0.
6. Amazon SNS (Simple Notification Service)
Amazon SNS is a fully managed messaging solution that provides low-cost infrastructure for bulk message delivery, primarily to mobile users. Users can chat directly with customers through system-to-system or app-to-person communication between decoupled microservice apps.
7. Amazon VPC (Virtual Private Cloud)
Amazon VPC enables you to set up a reasonably isolated section of the AWS Cloud where you can deploy AWS resources at scale in a virtual environment. VPC gives you total control over your environment, which includes the option to choose your own IP address range, creation of subsets, and arrangement of route tables and network access points.
Easily customize the network configuration of your VPC with flexible dashboard management controls designed for maximum usability. For example, users can launch public-facing subnet for web servers with internet access.
8. Amazon Auto-scaling
The AWS Auto-scaling solution monitors your apps and automatically tunes capacity to sustain steady, predictable performance at the lowest possible price. Seamlessly configure application scaling abilities for various resources across multiple services almost instantly.
Auto-scaling has a feature-rich and straightforward user interface that enables you to build scaling plans for various assets. These resources include Amazon EC2 instances and Spot Fleets, EC2 tasks, Dynamo DB tables and indexes, and Amazon Aurora Replicas.
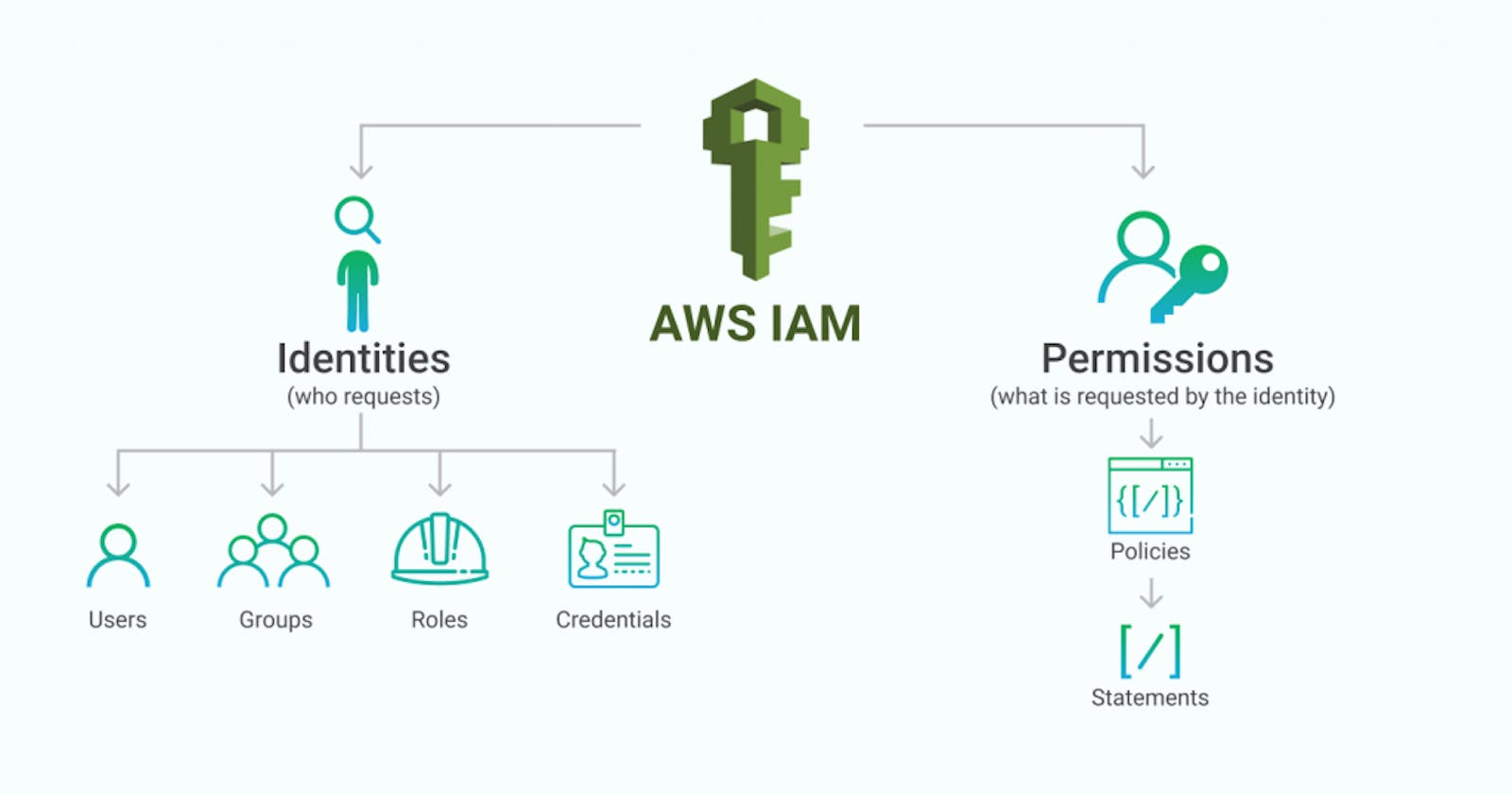
9. Amazon IAM (Identity and Access Management)
AWS Identity and Access Management provides secure access and management of resources in a secure and compliant manner. By leveraging IAM, you can create and manage users and groups by allowing and denying their permissions for individual resources.
There are no additional costs, people only get charged for the use of other services by their users.
IAM stands for Identity and Access Management and is a core component of Amazon Web Services (AWS). IAM allows you to manage users and their access to AWS resources in a centralized and secure way.
With IAM, you can create and manage AWS users, groups, and roles, and assign permissions to them to access specific AWS resources. IAM also provides features such as multi-factor authentication (MFA), password policies, and security certificates to ensure that only authorized users can access your AWS resources.
Using IAM, you can control who has access to your AWS resources, what actions they can perform on those resources, and from which locations they can access them. This enables you to enforce security policies and comply with regulatory requirements.
Overall, IAM is a critical component of AWS security and helps you manage access to your resources in a granular and controlled way.
To set up IAM (Identity and Access Management) in AWS (Amazon Web Services), follow these steps:
Sign in to the AWS Management Console with your AWS account credentials.
Navigate to the IAM console by clicking on the "Services" dropdown in the top left corner and selecting "IAM" under the "Security, Identity & Compliance" section.
Create users, groups, and roles as needed. Users are individual accounts with unique credentials, groups are collections of users with common permissions, and roles define a set of permissions that can be assumed by users or AWS services.
Create and assign policies to users, groups, and roles. Policies define the specific permissions that are allowed or denied for resources in AWS. You can create custom policies or use the pre-defined policies provided by AWS.
Set up MFA (multi-factor authentication) for added security. MFA requires users to provide an additional form of authentication, such as a code generated by a mobile app or a hardware token, in addition to their username and password.
Test your IAM configuration by logging in as a user and verifying that the permissions and policies are working as intended.